AWS Root Account Ownership
Introduction
Root account credentials are the key to securing your accounts against malicious or accidental security incidents, which is why SoftwareOne treat the storage and access to these credentials with the utmost due care and attention.
By holding the root credentials, SoftwareOne can enforce the Identity and Access Management (IAM) best practices laid down by AWS in protection of accounts.
Partnering with SoftwareOne to secure your accounts will protect your credentials, whilst providing the quickest possible response in an emergency.
Value of SoftwareOne Owning root Credentials
SoftwareOne employ rigorous security hygiene procedures and policies around the use of root accounts, including partitioning and isolation of root and MFA credentials. Following industry-recognised four-eyes principles, no individual at SWO may access both halves of a customer’s root credentials (password and MFA). Use of and changes made with these credentials are logged and audited.
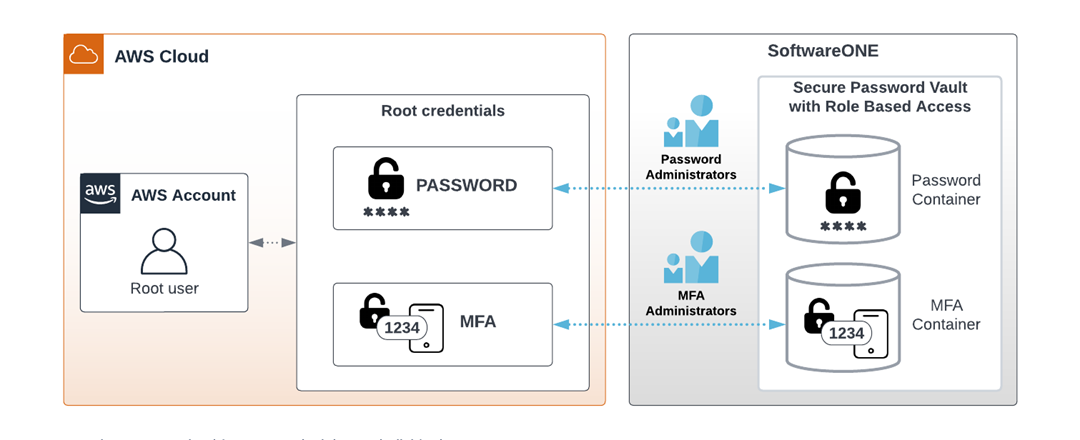
By SoftwareOne owning root, you are protected from being locked out in common security use cases, such as when malicious employees have locked access to accounts and purposely generated significant resource consumption, e.g. through crypto mining.
SoftwareOne will act as an extension of your teams; in a break-glass event where emergency access is required, this can be implemented more swiftly than by a direct relationship with AWS.
FAQs & Common Misconceptions
Why does SoftwareOne have to own the root credentials?
Under the CSP model and in common with other providers, SoftwareOne is accountable for payment of all AWS invoices. You are accountable for payment of all SoftwareOne invoices, including any discounts, non-standard payment terms, etc. As SoftwareOne owns the legal relationship with AWS, SoftwareOne require ownership of the root account.
Under the CSP model, AWS require that a SoftwareOne alias is the primary email address for the root credentials under the master payer account, to provide ongoing billing and invoicing through SoftwareOne and for communication between AWS and SoftwareOne billing teams for day-to-day resolution of billing queries and issues.
By holding the root credentials, SoftwareOne can enforce the Identity and Access Management (IAM) best practices laid down by AWS in protection of accounts.
I cannot make changes to my account using root credentials.
Regardless of whether a customer is consuming managed services, where SWO are accountable for the root account credentials, SWO are happy to make changes requiring root to customers' accounts, on their behalf.
I need root to make changes.
The vast majority of changes to an accounts and organisations do not require the use of root credentials. The following article from AWS describes the specific use cases where root is required: https://docs.aws.amazon.com/IAM/latest/UserGuide/root-user-tasks.html
If I want to move to another partner, SoftwareOne can block it as they own root.
Account transfers are subject to payment of outstanding invoices. SoftwareOne will always collaborate in good faith with customers who wish to move their accounts to another partner, ensuing a smooth transition. During transfer of accounts back to customer or other partner control, SoftwareOne will reset and provide the relevant credentials as required.
My credentials are safer if I store them myself.
SoftwareOne employ rigorous security hygiene procedures and policies around the use of root accounts, including partitioning and isolation of root and MFA credentials. Following industry-recognised four-eyes principles, no individual at SWO may access both halves of a customer’s root credentials (password and MFA). Use of and changes made with these credentials are logged and audited. This level of segregation and control is commonly not available or scalable 24/7/365 with many of our customers.
By SoftwareOne owning root, customers are protected from being locked out in common security use cases, such as when malicious employees have locked access to accounts and purposely generated significant resource consumption, e.g. through crypto mining.
For all customers on Simple for AWS v2 and newer, non-root access to accounts for SoftwareOne employees is controlled through federated identity and assumption of roles. This access is logged and audited, with activity linked to individuals.
For customers on earlier versions of Simple for AWS, access is via IAM user credentials, stored in a secure central vault. We encourage all customers to transfer to Simple for AWS v2 for further enhanced security and compliance, at no additional cost.
Why does SoftwareOne delete the access keys to root accounts?
Access keys provide programmatic access to accounts. As per industry-recognised AWS best practices, when onboarding customers, these keys are deleted, ensuring that a bad actor may not utilise the keys for malicious activities in the future.
When onboarding, I don’t want to provide my root account credentials as the password is used across other systems or is pattern-based.
As per industry best practices, SoftwareOne would always recommend that customers do not re-use passwords. Prior to transferring root account credentials to SoftwareOne, the root password should be reset to a unique password.
